Knowing what to look for and what tools to use when conducting OSINT for supply chain risk management can give organizations a competitive edge, resilience to cyberattacks and protection from non-compliance.
Organizations today cannot work in isolation. You must utilize resources from diverse suppliers in different locations to get a competitive edge. Doing business with third-party vendors can introduce numerous benefits, such as cutting costs, saving time and providing your customers with high-quality products and services. However, this comes with a price: Security!
Expanding the supply chain will require doing business with many vendors, which will expand your attack surface and increase your risk exposure. Many risks are impacting your supply chain. A recent study by WTW, which surveyed 800 senior decision-makers across different industries worldwide to understand their supply chain risks and challenges, found that the main factors underlying supply chain risks can be summarized as follow:
- Economic uncertainty (32%)
- Inflation (26%)
- Cyber risks were rated by 34% of respondents as highly impactful and by 54% as moderately impactful on supply chains
The increased complexity of today's global supply chain networks necessitates assessing the risks associated with your external vendors. Open-source intelligence (OSINT) can provide investigative capabilities to mitigate many dangers associated with the supply chain at a cost-effective price. However, before we start discussing how OSINT can help avoid many supply chain risks, it is worth examining the technological risks impacting the supply chains of global organizations.
Technological risks impacting modern supply chains
The WTW survey found that cyber risks are among the top risk factors impacting the supply chain. The most prominent cyberthreats are:
- Cyberattacks against the supply chain: Cyberattacks such as those using malware, ransomware and other malicious programs could disrupt normal supply chain operations and impact accessing critical systems and resources of third-party vendors.
- Data breach: A successful cyberattack can lead to breaching suppliers' sensitive information or exposing trade secrets to unauthorized parties. This can result in compliance violations and paying huge fines as penalties and legal fees.
- IT infrastructure failure: A cyberattack against the supply chain can lead to network outages or loss of electricity, which will impact IT infrastructure and cease normal work operations.
- Integration challenges: Integrating different IT systems to work harmoniously can be challenging when each vendor has different software and IT platforms. This fact will also lead to more security vulnerabilities in outdated IT systems and software.
- Manual process: Some vendors may still use manual processes to fill some work needs. This increases the visibility problem across the supply chain as not all supplier work processes can be audited.
- Skill gaps: Not all vendors across the supply chain will have the same technological knowledge, especially in emerging technologies, such as AI, IoT and blockchain, as the rest. The talent gap will prevent full collaboration across the supply chain.
How can OSINT be used to mitigate global supply chain risks and vulnerabilities?
OSINT can be helpful to lower supply chain attacks through the following:
Investigating suppliers
OSINT can be used to gather wide arrays of information to determine supply chain risk. Here’s a list of various assessments to perform on suppliers and some OSINT tools to use:
- Checking supplier corporate information: Open Corporates, Annual Reports and SEC are examples to find information about your supplier corporations.
- Financial information: EDGAR | Company Filings
- Global financial stability: Check the financial stability of the countries where our suppliers operate. There are many sources to get such information, such as International Monetary Fund and World Bank.
- Commercial partners: Factiva provides high-quality business content from 200 countries and in 26 languages by integrating more than 35,000 sources from the Dow Jones Interactive and Reuters Business Briefing.
- Compliance issues: The GDPR Enforcement Tracker website to see a current list of all companies that were subject to fines and penalties because they have breached the EU General Data Protection Regulation (GDPR).
- Public reputation: Inspect vendors social media profiles and read customers feedback regarding their products and services to assess their reputation and how they handle customers feedback.
- Verifying vendor physical location: Use Google Maps and Google Street View (if the address is supported) to verify the current address of a vendor. We can also check a vendor's registered physical address in Open Corporates and Crunchbase to verify their address.
Investigating vendors’ executives and key stockholders
Your suppliers could have legal issues or participate in illegal activities in some countries that are subject to sanctions. Investigating supplier top management and key stockholders is necessary before engaging in any business relation with them. There are numerous resources to investigate individuals' backgrounds. The following are some resources to start with:
- List of countries sanctioned by the USA: Check the Office of Foreign Assets Control for a detailed list of sanctions programs and country information.
- List of individuals and companies blocked by the USA: Check OFAC website’s SDN list (specially designated nationals and blocked persons).
- Search for a person's social media profile: Once you find the first account, for example a person's Facebook account, you can search for similar accounts having the same username on other social media platforms. instantusername.com and usersearch.org allow searching for a particular username across many social media websites.
- Use people search engines: Find information about any individual, such as their address, employment history, social media profiles, contact information and criminal records. Tools to use include Truth Finder, Unmask for people search and Numberbook to fetch caller ID.
Discover technological infrastructure utilized by suppliers
Some foreign suppliers may not be transparent with you regarding their IT systems. For example, some suppliers may fear losing your partnership contract if they disclose using outdated IT infrastructure. OSINT can help us discover suppliers' IT infrastructure through various means. The easiest one is checking the supplier country's local job websites and reading the job posts announced by this supplier. For example, in Figure 1, I was able to find many IT systems used by a specific company by checking its job posts and reading a few of its employees' work profiles on LinkedIn (see Figure 2).
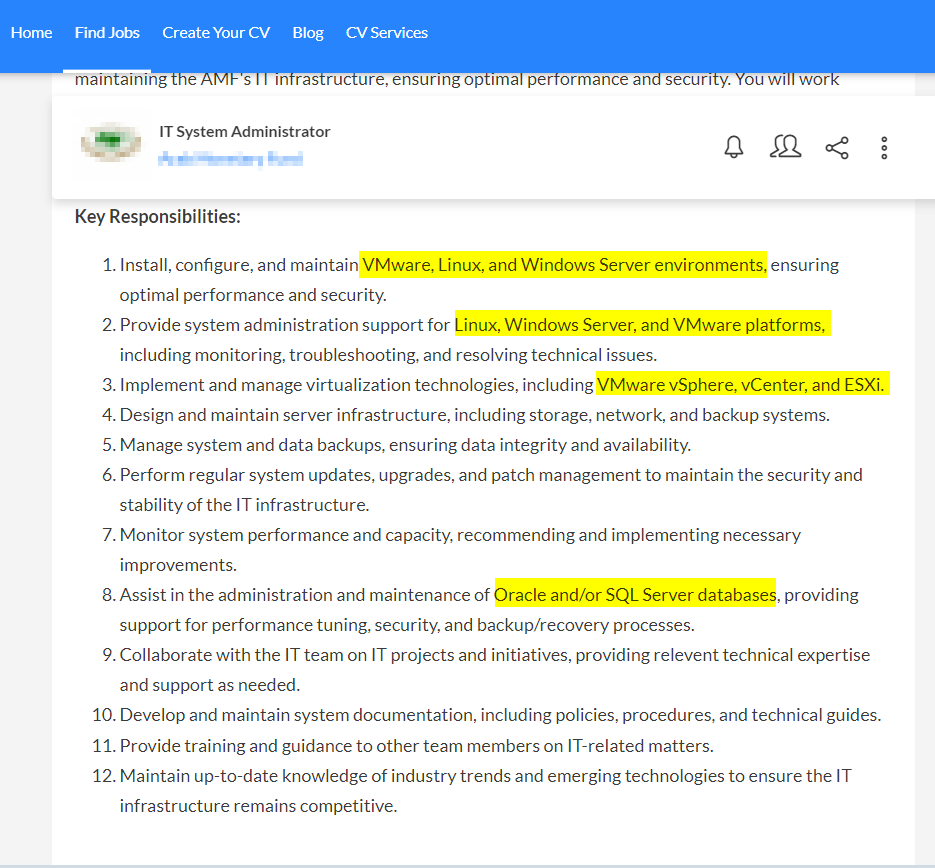
Figure 1 | Job vacancy websites can reveal important information about any company internal IT infrastructure
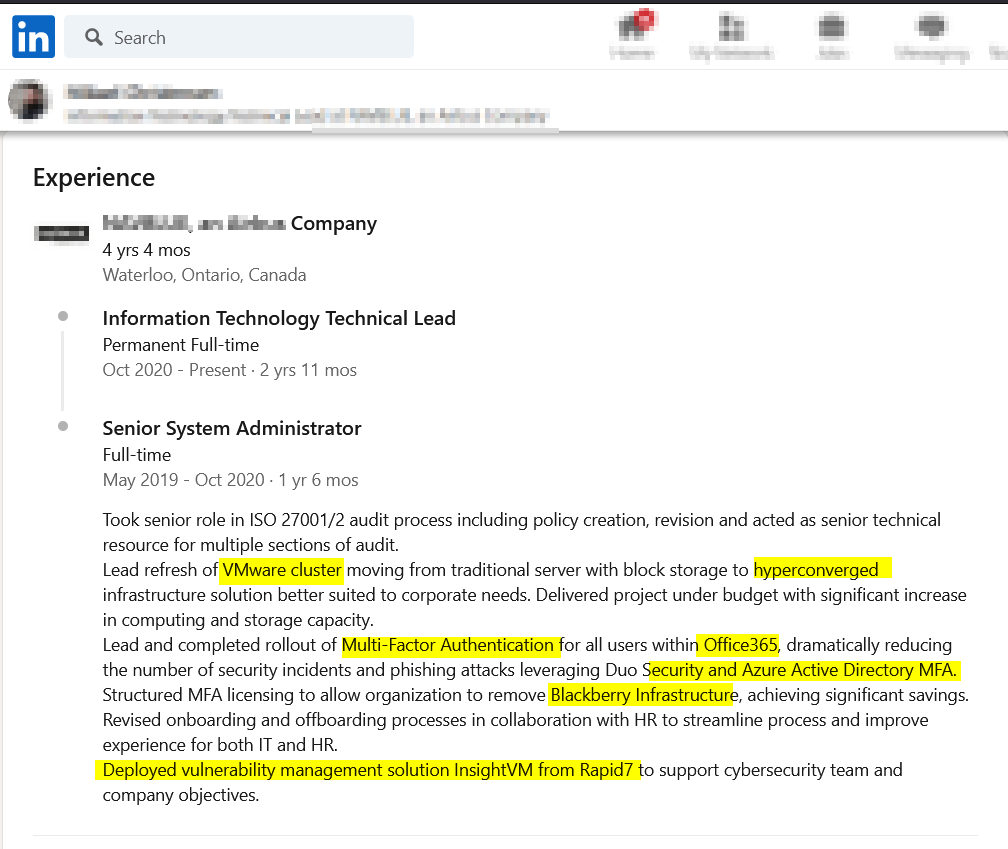
Figure 2 | Employees work experience on LinkedIn can reveal technical information about suppliers' IT infrastructure and cybersecurity defenses
Cyber risks associated with suppliers
Regardless of the security solutions you are using to protect your IT environment, a vulnerability in your supply chain can make you prone to cyber risks. For instance, many high-profile data breaches happened because of supply chain vulnerabilities. The most noticeable incidents caused by supply chain vulnerabilities are:
- SolarWinds attack: Threat actors exploited the update mechanism of SolarWinds network management solution and inserted a malicious code within it. The malware was distributed to all clients using this software and resulted in accessing their IT environment and data. Among the victims were government agencies and high-profile private organizations.
- Kaseya attack: Kaseya is a managed service provider (MSP) that provides remote management software. The attack, which took place in 2021, resulted in distributing ransomware to all corporate clients using the Kaseya software solution.
To find information about corporations that previously suffered from a data breach, we can check these resources:
- For California-based companies, check State of California Department of Justice Data Security Breaches
- Commonwealth of Massachusetts data breach reports
- Delaware data security breach database
- U.S. Department of Health and Human Services list data breaches that impact protected health information affecting 500 or more individuals
- Have I been pwned tells you if a particular supplier email address, phone number or password was included in a previous data breach (see Figure 3). F-secure provides similar functionality.
- Identity Theft Resource Center, this website allows finding previous breaches related to a particular company
- DLA Piper provides a list of all data protection laws worldwide
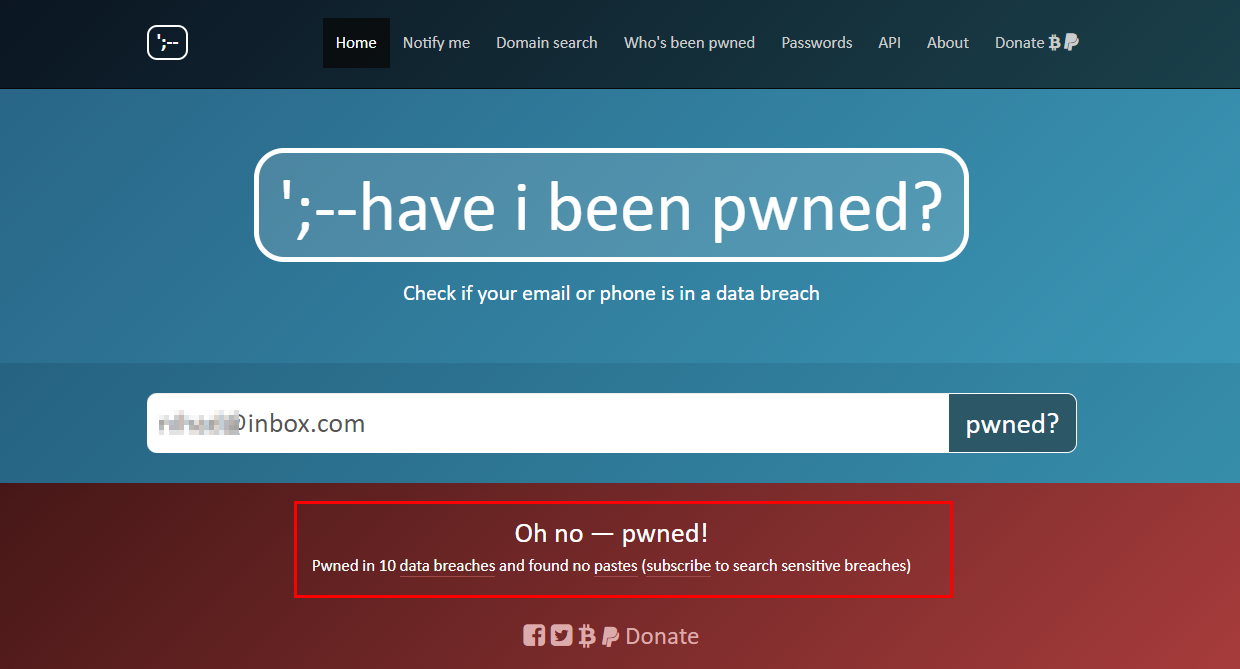
Figure 3 | https://haveibeenpwned.com Allows you to check if your email was included in previous data breaches
Dark web monitoring
Dark web networks, such as Tor and I2P, are commonly utilized by cybercriminals to sell leaked information. These places should be monitored for exposed information related to suppliers and for any malicious signs that impact your organization's supply chain.
As we saw, OSINT can be utilized as an early warning system to prevent different risks to your supply chain. For instance, by using OSINT techniques, you can detect early signs of threats within your entire supply chain, such as:
- Political instability in your suppliers’ countries
- Monitor the financial situation of your suppliers; for example, avoid dealing with suppliers who could be exposed to bankruptcy
- Prevent cyber risks against your organization before they happen by monitoring darknets for leaked supplier information that may affect your supply chain security
- Avoid non-compliance status by avoiding dealing or using software components from suppliers with high-risk profiles (located in sanctioned countries or have weak security controls to protect their IT assets).
The breadth of publicly available resources makes leveraging OSINT a must for any organization operating on a global stage and wants to incorporate resources from diverse third-party suppliers into its products/services lines. OSINT will help organizations gain a competitive edge while enhancing their resilience to cyberattacks.
Tags Dark web research OSINT research Social media

